Security is not a technical problem. It’s an executive decision system.
A cybersecurity maturity framework for growing companies facing audits, enterprise customers, and real accountability.
Most companies don’t fail security audits because of hackers
-
Controls exist, but no one owns them
-
Documentation is scattered or outdated
-
Security decisions happen under pressure
-
Answers change depending on who you ask
The problem is not lack of tools.
It’s lack of a system.
Compliance checklists don’t create maturity
Explain that frameworks, tools, and controls without structure create false confidence.
Cybersecurity maturity is the ability to respond clearly when someone demands answers
What is the Cybersecurity Maturity Framework?
A decision-making and execution framework designed to help CEOs and leadership teams understand, prioritize, and operationalize cybersecurity — without turning it into a technical black hole.
Key characteristics:
-
Executive-level clarity
-
Control ownership and accountability
-
Risk-based prioritization
-
Evidence-ready by design
-
Aligned with real business pressure
Who This Is For
This framework is designed for companies that are growing
Good fit list:
-
SaaS / Fintech / B2B services
-
10–250 employees
-
Selling to enterprise customers
-
Facing SOC 2 / ISO / client security reviews
-
Dealing with insurance, legal, or board pressure
Not a fit (important):
-
Companies looking for “just a tool”
-
Teams expecting security to be solved by IT alone
-
Organizations not ready to take ownership
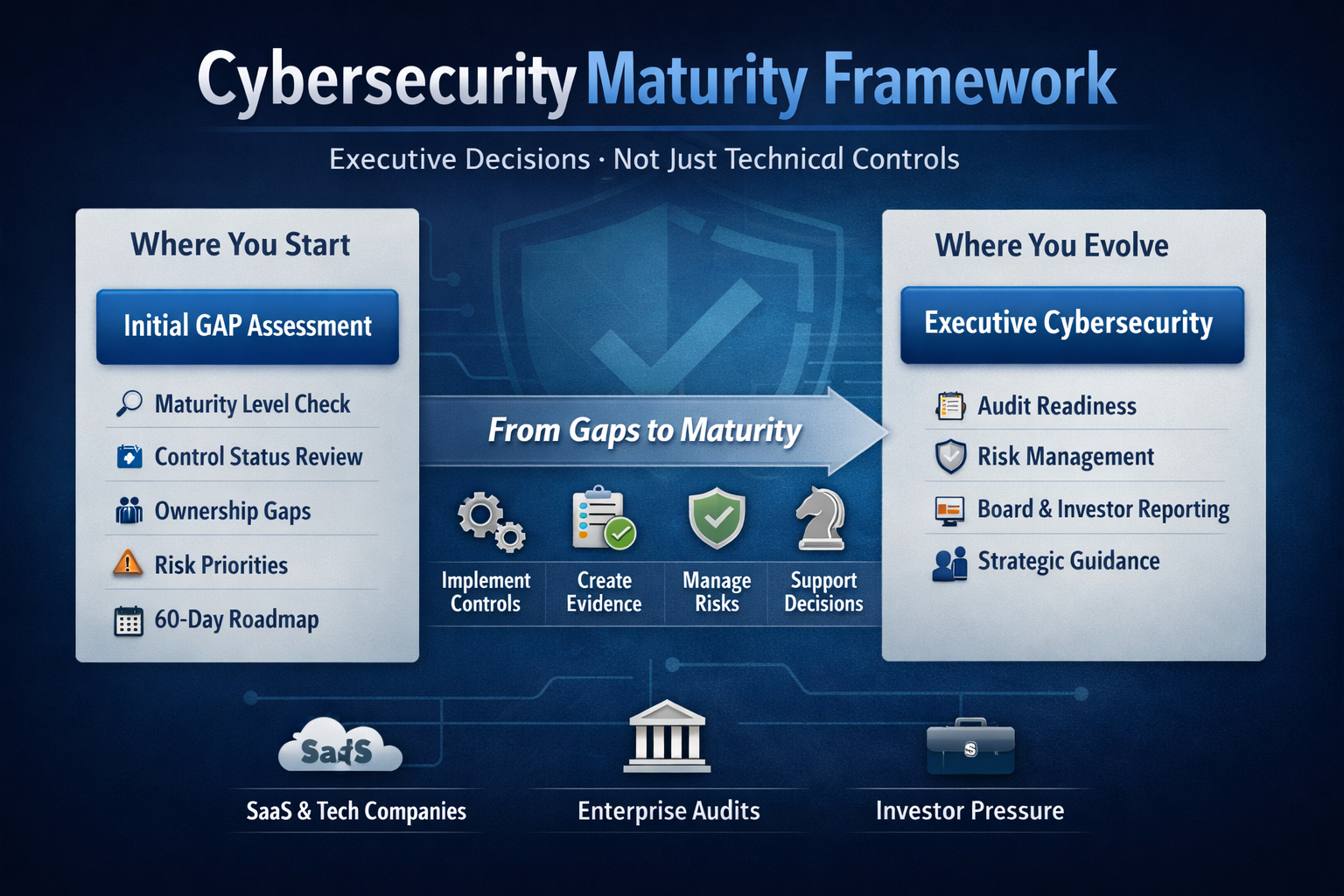
The 3-Stage Model
Stage 1 — Initial GAP (60 Days)
Goal:
Understand where you really stand.
Outputs:
-
Maturity level assessment
-
Control status (compliant / partial / missing)
-
Ownership gaps
-
Risk-based priorities
-
3–6–12 month roadmap
Stage 2 — Full GAP + Implementation
Goal:
Turn the roadmap into reality.
Focus:
-
Control implementation
-
Evidence creation
-
Internal ownership
-
Execution cadence
Stage 3 — Executive Cybersecurity (VIP)
Goal:
Sustain maturity over time.
Focus:
-
Decision support
-
Ongoing risk management
-
Audit readiness
-
Strategic guidance
This is not a consulting checklist
Differentiators:
-
Designed by a Fractional CISO, not a vendor
-
Focused on executive decisions, not tools
-
Built to reduce uncertainty, not add complexity
-
Designed to stand under external scrutiny
Key line:
The framework exists so you’re never forced to improvise under pressure.
This usually starts with an uncomfortable email
Examples:
-
“Please complete this security questionnaire”
-
“We need SOC 2 evidence”
-
“Our insurer needs updated controls”
-
“The board is asking questions”
Closing:
When that happens, maturity is revealed instantly.
